Raketa Travel supports single sign-on (SSO) technology through SAML 2.0. The SAML 2.0 identity provider (IDP) can be any system, including your own Active Directory Federation Services (ADFS) server installation.
ADFS is a service provided by Microsoft as a standard Windows Server role. It provides the ability to log into WEB services using existing Active Directory authentication data. In most cases, this is the login / password for a domain account.
1. Preparation
To use ADFS, you must have:
- Server running Microsoft Windows Server. The screenshots in this tutorial were taken using the 2016 version.
- An Active Directory installation in which all users have a completed e-mail address.
- SSL certificate for your ADFS login page.
We provide:
- Login URL in the format https://raketa.travel/sso/acs?clientId=YOUR_CLIENT_ID.
- Logout URL in the format https://raketa.travel/sso/slo?clientId=YOUR_CLIENT_ID.
After all necessary settings, you should provide:
Full table File.xlsx
- Entity ID – Your internal corporate portal URL.
- SAML SSO URL – Your login page URL, which we will use to redirect users to your identity system.
- Remote logout URL – Your URL, which we will use to redirect users after they log out.
- X509 Certificate – auto-generated certificate file. You need to download, item 5.
After meeting the basic requirements, install ADFS. Configuration and installation are detailed in the Microsoft Knowledge Base:
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/deploying-a-federation-server-farm
After ADFS is fully installed, see the value for "SAML 2.0 / W-Federation" in the "Endpoints" section. If you did not change the settings during installation, the value will be "/ adfs / ls /".
2. Adding a Relying Party Trusts
At this point, you are ready to set up communication between ADFS and Raketa Travel. This relationship is established through the Relying Party Trust..
Open the Relying Party Trusts directory in the AD FS Management snap-in. In the action bar, select Add Relying Party Trusts. This action will launch the configuration wizard.
In the Select Data Source step, select Enter data about relying party manually.
In the next step, provide any desired name and notes.
If the next step prompts you to select a profile, select "AD FS profile".
At the step "Configure Certificate", you do not need to specify an additional certificate.
In the Configure URL step, enable SAML 2.0 WebSSO support and enter the login URL we provided in the format https://raketa.travel/sso/acs?clientId=YOUR_CLIENT_ID
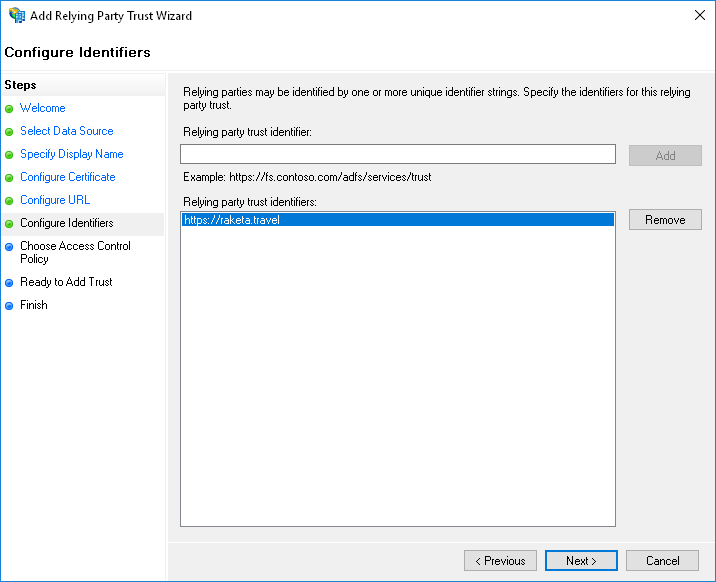
In the "Configure Identifiers" step, enter "https://raketa.travel" and click the "Add" button.
In the next steps, you can configure additional parameters that apply to this Relationship.
3. Configuring the claim issuance policy
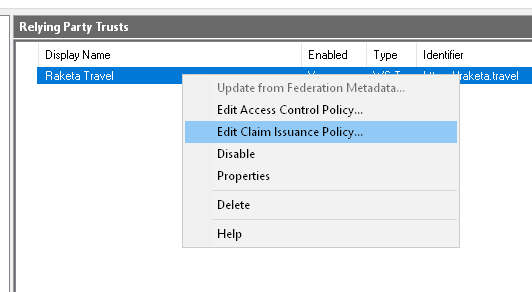
After you create the Relying Party Trust, you need to configure the claim issuance policy. To do this, from the Relying party trusts context menu, select Edit Claim Issuance Policy.
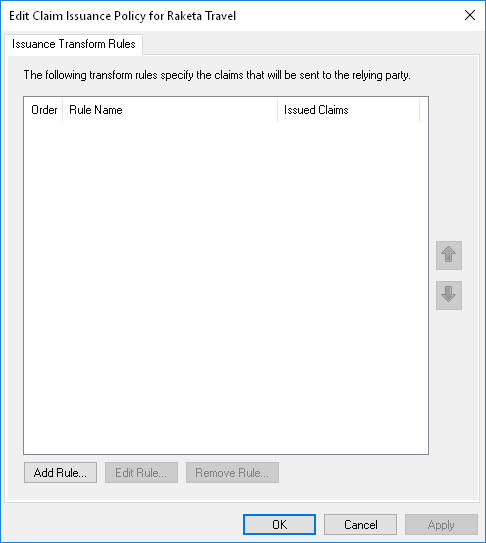
In the window, you need to add 2 rules.
First rule:
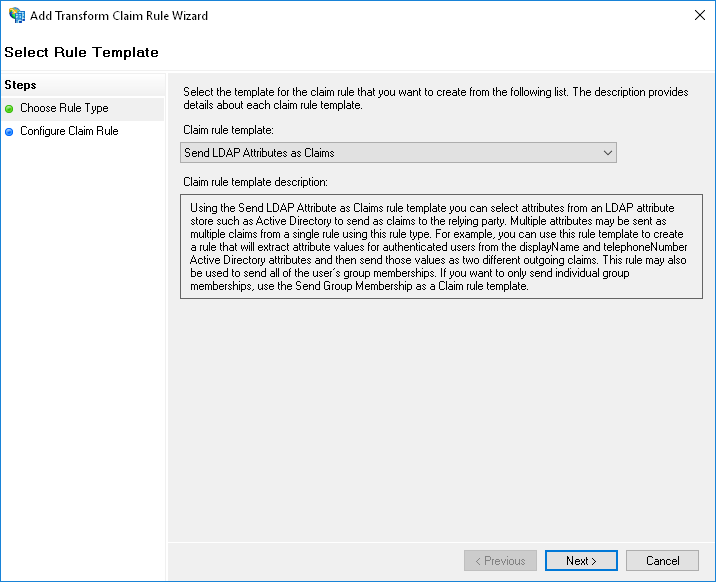
- Claim rule template: Send LDAP Attributes as Claims.
- Attribute store: Active Directory.
- Mapping: E-Mail-Addresses -> Email Address.
Second rule:
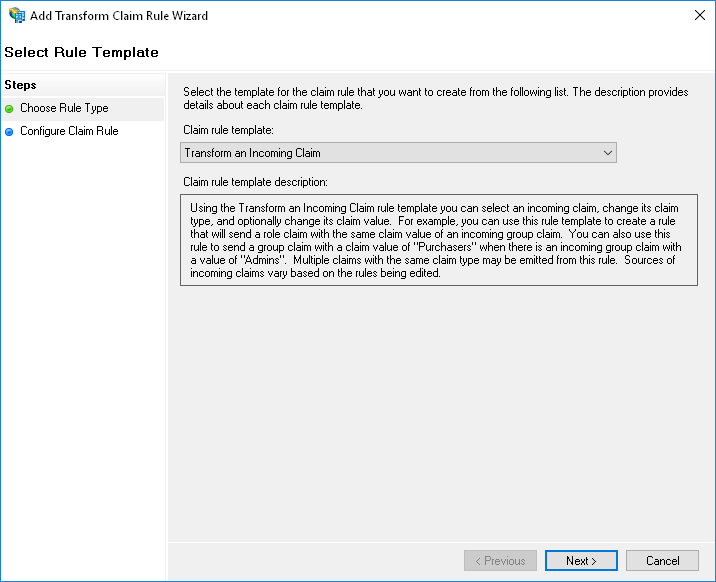
- Claim rule template: Transform an Incoming Claim.
- Incoming Claim Type: Email Address.
- Outgoing Claim Type: Name ID.
- Outgoing Name ID format: Email.
- Pass through all claim values – selected.
4. Additional Configuring: Relying Party Trusts
After configuring claim issuance policies, you need to further configure Relying Party Trusts. To do this, in the context menu of the Relying Party Trusts, select "Properties".
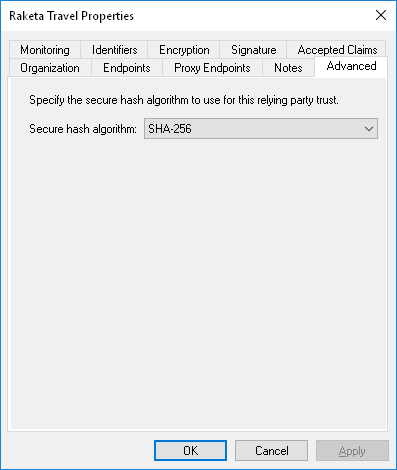
On the "Advanced" tab, make sure that the SHA-256 hashing algorithm is set.
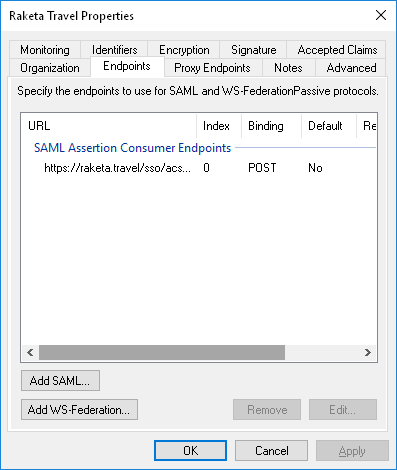
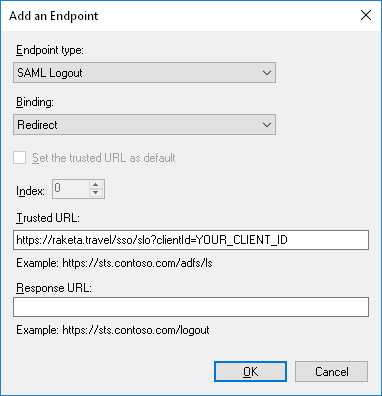
On the Endpoints tab, add an endpoint. To do this, click the "Add SAML" button. In the window that opens, specify:
- Endpoint type: Завершение сеанса SAML.
- Binding: Redirect.
- Trusted URL: Logout URL that we have provided in the format https://raketa.travel/sso/slo?clientId=YOUR_CLIENT_ID
5. Obtaining of the token certificate
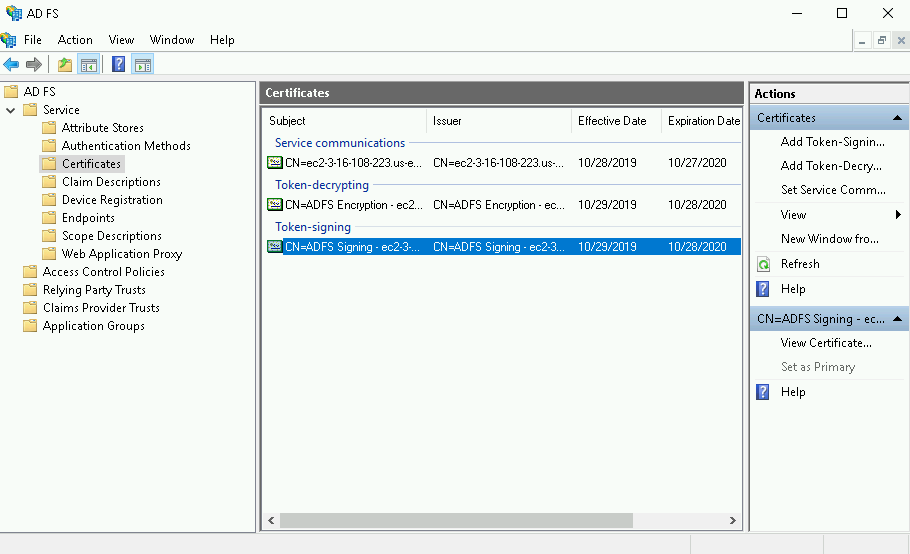
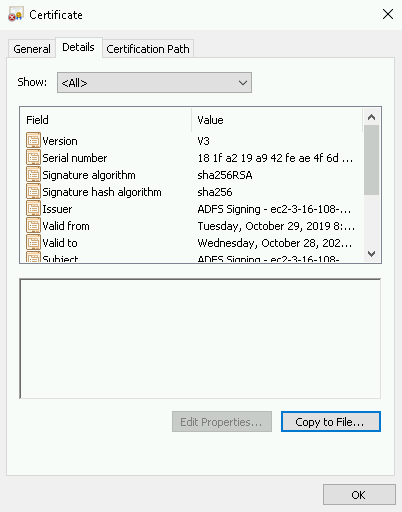
Open the ADFS management snap-in, select ADFS > Service > Certificates, then double-click on the certificate under Token-signing. You can also right-click the field, then select View Certificate in the context menu.
On the Certificate screen, open the Details tab, select Copy to File, then select OK.
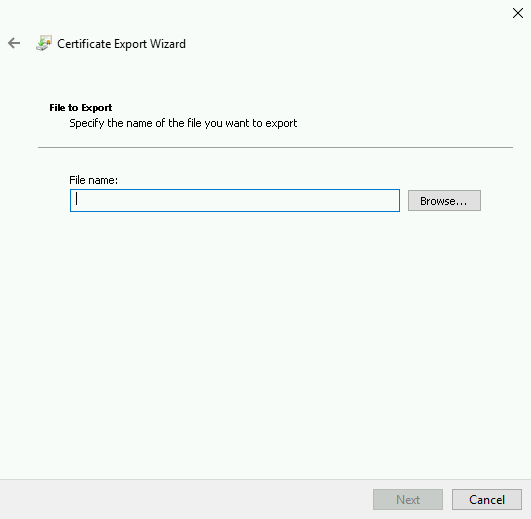
On the Certificate Export Wizard screen, select Next.
Select Base-64 encoded X.509 (.CER), then select Next again.
On the Certificate Export Wizard screen, select Browse to specify the location where you want the Identity Provider Certificate to be exported, then specify the file name.
Select Save. On the Certificate Export Wizard screen, verify the file path is correct, then select Next.
In the Completing the Certificate Export Wizard, select Finish, then select OK to confirm the export was successful.